Warning
This article is focused on Blueteam and not from an offensive point of view. The few offensive elements mentioned will intentionally not be detailed.
Overview of Active Directory Infrastructures - Functioning and limitations of the 3-TIER model
In this first article, we will cover one of the key concepts in Active Directory security: the 3-Tier model.
The goal here is to understand how this model works, why it is necessary to implement it, and what its limitations are.
It is important to note that we will take a defensive approach in this article, so any offensive elements that may be mentioned will intentionally not be detailed.
Active Directory: a central component targeted by many attacks
Active Directory plays a central and particularly critical role within IT systems. This criticality makes it a highly targeted component for attackers, and therefore extremely important to secure properly.
However, the multitude of elements that make it up broadens its attack surface and introduces vulnerabilities and configuration flaws that attackers can exploit. Examples include vulnerabilities such as Bluekeep, PetitPotam, PrintNightmare, MS08-067, MS17-010, etc.
The resulting attack techniques are mostly known and understood. Among those used, we can mention the following:
- ASREP Roasting, which allows an attacker to obtain a user’s TGT and potentially its password.
- Kerberoasting, which allows an attacker to retrieve a user’s TGS and potentially the password of the account running the targeted service associated with the TGS.
- Pass The Hash, which allows an attacker to use the cryptographic hash of a user’s password instead of the password itself during NTLM authentication.
- Silver/Golden Ticket, which allows an attacker to forge service authentication tickets and thus grant themselves arbitrary rights.
Despite this knowledge of vulnerabilities and attack techniques, companies struggle to achieve a sufficient level of security. Indeed, every year, Active Directory continues to play a prominent role in the compromise of IT systems during attacks.
This security debt can be explained by various factors, such as the technical difficulty of certain remediations, their operational impacts, organizational barriers, economic considerations, etc.
In any case, it is evident that Active Directory, as it is deployed and maintained in an enterprise IT context, is destined to remain vulnerable.
Given this situation, it becomes urgent to find measures to limit the impact of an attack on the IT system and to improve its resilience. This is where the 3-Tier model comes into play.
The 3-Tier Architecture - A first line of defense against attacks on Active Directory?
During an attack on an information system, the success of the attacker largely depends on their ability to move through the system. Indeed, it is rare for an attacker to directly compromise a domain controller or the critical resource they are targeting. Instead, they will attempt to exploit attack paths to ultimately reach their target.
Given this, we can deduce that an attacker who compromises an initial resource but is unable to move within the system would also be unable to spread their attack and reach their target. The key to overall security might then lie in segmenting the system into different zones.
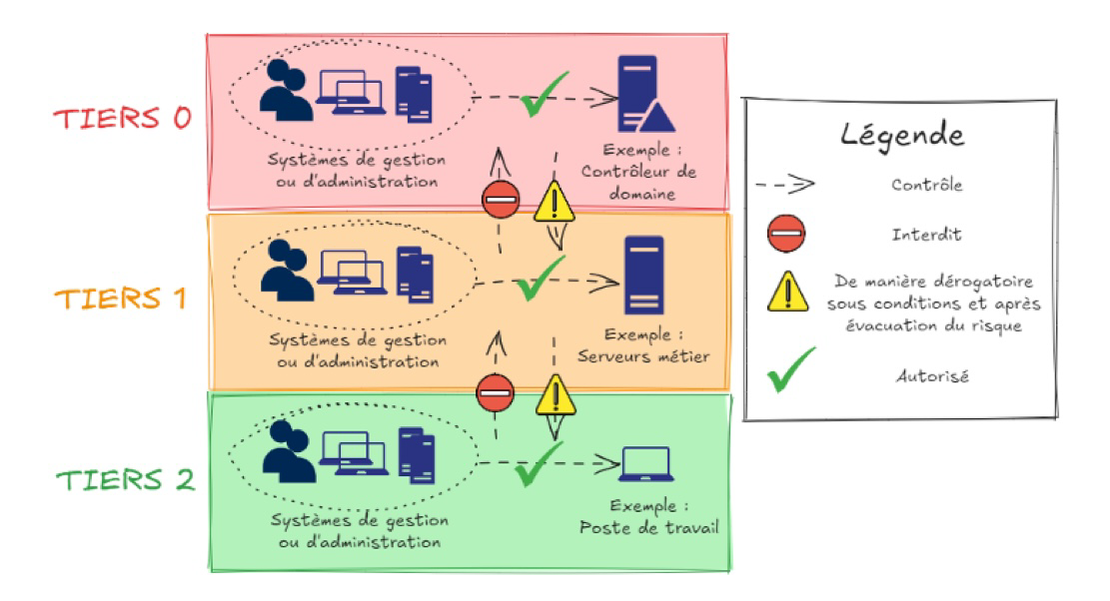
Following this logic, a model for segmenting the system into “Tiers” was proposed by Microsoft. This division into logical subsets aims to separate resources based on their level of trust (or criticality). The goal of this model is to contain a potential compromise within the infected zone, preventing it from spreading to other trusted zones. The categorization of the zones ensures that the most sensitive ones are the least exposed, while the less sensitive ones are the only ones directly exposed to threats.
The model is described as follows:
- Tier 0, the trust core of the organization: These are the resources with the highest administrative privileges and are therefore the most critical. These privileges grant control over all Active Directory resources, including domain controllers. A compromise of this Tier means the compromise of the entire Active Directory and the potential establishment of backdoors that are extremely difficult to detect.
- Tier 1, trust in the organization’s business assets: These include business assets and related support assets (storage, processing, etc.). Examples include source code management servers or equipment in a production chain. Generally, this Tier encompasses resources that are critical to the business from an operational standpoint.
- Tier 2, trust in workstations: This includes all IT equipment such as workstations, industrial consoles, printers, etc. These resources are less critical but far more exposed to threats.
Implementing this tiering model allows for the application of differentiated security policies tailored to the criticality level of each Tier.
The scope of this model’s application must also be clearly defined. Although it is recommended to apply it to the AD forest, it is important to manage trust relationships that may exist with other potential forests and ensure that these relationships do not increase the permeability of the segmentation. Regular audits focused on these considerations are also recommended. Since the AD domain does not present a real security boundary, it is advised not to limit the application to this perimeter alone.
The rigorous implementation of this model can be particularly challenging and is done through an iterative process. An incomplete implementation can leave residual attack paths in the system. As the system is constantly evolving, it is essential to approach segmentation as part of a continuous improvement process.
To ensure the relevance and completeness of the segmentation, it is absolutely essential to conduct a thorough analysis of attack paths. This analysis will then allow for the correct categorization of each resource into the appropriate Tier, so that the corresponding policies can be applied. The variety of potential attack paths and the complexity of many of them make their identification particularly difficult. It is generally recommended to consult professionals with advanced technical expertise. Tools like Bloodhound can help map weak control paths.
Subsequently, resource categorization follows this logic: if an attack path is identified from resource A to resource B in a more sensitive Tier, resource A should be categorized in the same Tier as resource B. Thus, to avoid having a disproportionately large number of resources in Tier 0, it is essential to eliminate or mitigate the identified attack paths. Naturally, this step becomes more complex as the system grows, but it is through this approach that effective and satisfactory segmentation of the system can be achieved.
In general, the goal is to minimize exposure for each Tier (particularly Tiers 0 and 1) by reducing interactions with other trust zones. This requires a solid understanding of the system, its flows, and its applications in use.
Mitigating attack paths also involves hardening the systems and software in use within the system. This includes leveraging the various configuration options of these systems and software to elevate their security level.
Additionally, to maintain this segmentation, system administration must be separated from its normal usage. This applies to both the hardware used (dedicated administration workstations) and the accounts used. This principle also applies at the Tier level: usage and administration of a Tier are separated, and the administration of two different Tiers is also separated. By following such practices, the segmentation remains secure.
This objective is particularly approached through fine-grained delegation of administrative rights. This is absolutely crucial. The principle is to minimize the use of Tier 0 administrative accounts by delegating necessary privileges to lower-Tier administrative accounts, while respecting the principle of least privilege and the RBAC model.
The limitations of the model
Although this model has already proven to be significantly effective in containing attacks and limiting their spread within the system, it is still far from perfect. Indeed, the segmentation is done between the Tiers, but very little within the same Tier, meaning that lateral movement within a Tier is hardly restricted. Neglecting this aspect would be a major mistake; for example, if Tier 1 is compromised, while the attacker would be blocked from moving towards the core of the network, they would still have the ability to compromise all of the company’s business resources.
So, wouldn’t it be possible to take this model even further to reduce both inter-Tier and intra-Tier movement?
In our upcoming articles, we will discuss another Active Directory architecture model that addresses this issue, as well as its limitations and potential solutions. We will also delve into the more technical aspects of implementing this model.